BQT Biometrics Australia: Blazing A Trail in Biometric Protection Modern Technology
BQT Biometrics Australia: Blazing A Trail in Biometric Protection Modern Technology
Blog Article
Maximizing Service Defense: The Ultimate Overview to Electronic Protection Solutions
In the busy and ever-evolving landscape of business protection, the dependence on electronic safety options has become paramount for guarding useful assets, personal information, and keeping functional continuity. In this overview to electronic security solutions, we will certainly explore the most recent patterns, cutting-edge modern technologies, and ideal methods to fortify your service against prospective risks and vulnerabilities.
Relevance of Electronic Safety Solutions
When thinking about the defense of assets and delicate details, the significance of digital safety and security remedies can not be overstated. In today's interconnected world, where cyber threats are continuously advancing and ending up being more advanced, organizations must prioritize carrying out robust digital safety and security procedures to safeguard their data and operations. Digital safety and security remedies encompass a wide variety of modern technologies and practices developed to resist unapproved accessibility, information breaches, malware, and other cyber risks.
Among the essential benefits of digital safety and security options is their capability to supply real-time monitoring and hazard detection. BQT Electronic Security. Via devices like breach discovery systems, firewalls, and safety and security information and event management (SIEM) systems, companies can proactively determine and reply to protection occurrences before they intensify into significant breaches. Additionally, electronic security services assist make sure conformity with industry laws and requirements, safeguarding businesses from possible lawful and financial repercussions
Kinds of Electronic Safety And Security Systems
Given the critical value of digital safety options in safeguarding services against cyber risks, it is crucial to explore the various types of digital security systems available to enhance defense and durability. One of the most common kinds of digital protection systems is the firewall software, which acts as a barrier between a business's internal network and outside networks, filtering system out possibly dangerous information. By using a combination of these electronic protection systems, services can develop a robust defense against different safety and security risks.
Implementing Accessibility Control Measures
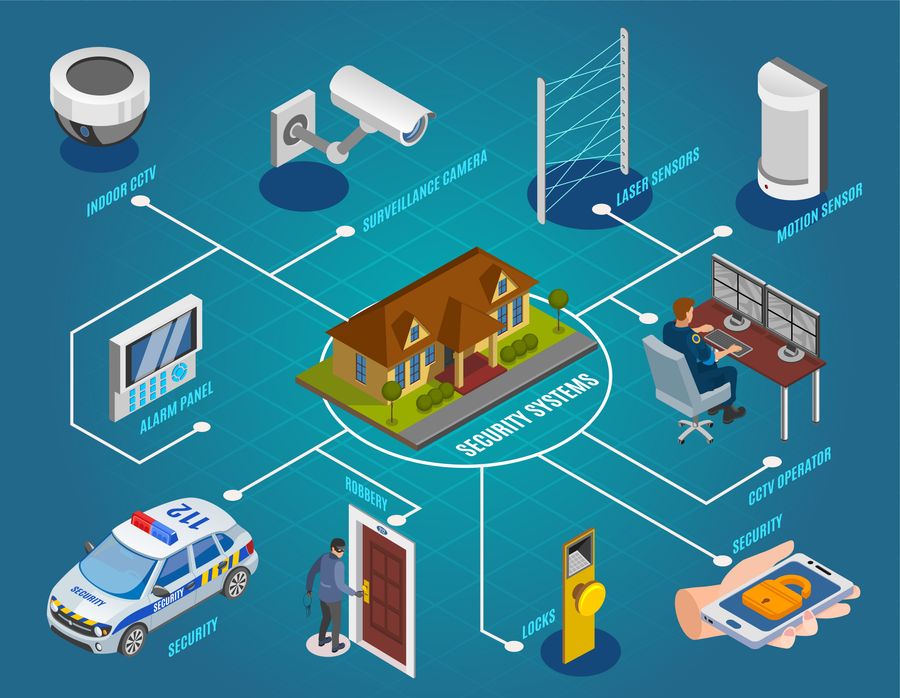
In addition, accessibility control measures can be incorporated with monitoring systems to monitor and tape-record people' movements within safeguarded areas. This assimilation enhances security by giving an extensive introduction of that is accessing certain places at any kind of offered time. Furthermore, accessibility control systems can be configured to restrict access based from this source on time, area, or private qualifications, allowing companies to customize safety and security protocols according to their particular needs.
Cybersecurity Finest Practices
To enhance general security stance, carrying out robust cybersecurity finest practices is necessary in securing digital possessions and information stability. One fundamental practice is ensuring normal software application updates throughout all gadgets and systems to patch vulnerabilities promptly. Using strong, unique passwords and implementing multi-factor verification adds layers of protection versus unapproved gain access to. Carrying out regular security audits and evaluations helps determine weak points and locations for improvement. Staff member training on additional reading cybersecurity awareness is vital in avoiding social design strikes and ensuring a security-conscious workforce.
Establishing an extensive event response plan enables swift and efficient reactions to safety breaches, minimizing prospective damage. Securing delicate information both en route and at remainder offers an added barrier versus information violations. Applying access controls based on the principle of the very least advantage limits the direct exposure of essential systems and info to just those who require it for their duties. Regular backups of information ensure that in the occasion of a ransomware attack or data loss, vital info can be recouped. Accepting a proactive technique to cybersecurity with continuous tracking and risk knowledge helps detect and minimize potential risks prior to they escalate. By incorporating these best methods right into cybersecurity approaches, businesses can fortify their defenses versus developing continue reading this cyber threats.
Security and Tracking Solutions

Video clip monitoring services offer remote monitoring capabilities, allowing accredited personnel to keep an eye on the premises even when off-site. In addition, advanced functions like activity discovery, facial recognition, and permit plate acknowledgment improve the total safety posture of the organization. Incorporating security systems with security system and gain access to control further reinforces the protection infrastructure, allowing an aggressive feedback to potential security breaches.
Final Thought
In conclusion, electronic protection options are necessary for making best use of organization security. It is essential to spend in the ideal electronic security systems to make certain the safety and security and safety of the organization.
Report this page